Where Can I Find Tenant Id in Azure Ad
Intro
When I started learning Azure Active Directory, I was pretty overwhelmed past the Microsoft documentation, which in my opinion was beautiful complicated (peculiarly for people WHO don't have much feel at configuring some OAuth Mandate Servers — like me). Since I've fagged a lot of fourth dimension reading Microsoft documents, blogs, and have experimented by myself and with my teammates (thanks Tim!), I'd like to portion with you what I've noninheritable about AAD during this time.
I've ever been a big fan of the "Example first" way. Victimisation this approximation, I'm going to walk you through with some examples and, hopefully, after reading this instructor, you tail end approaching Microsoft Documentation fearlessly.
This article assumes that you already have a good understanding of OAuth 2.0, especially Authorization Code menses. If you don't, I highly recommend you watch this cracking television:
Present is the OAuth terminology that bequeath be utilized throughout this tutorial.
I also assume that you have your ain tenant in Azure and it's associated with the valid subscription. If not, you can regain tutorials how to do IT present and here.
Throughout this tutorial I'll be using only Azure AD End point V2, however, in one surgical incision I'll sum in some base differences 'tween V1 and V2.
Creating applications
First, we'll create two applications in AAD, that will represent some Client and Resource Applications. You can practice this by following these steps:
Your Cerulean Active Directory instance -> App enrolment -> New registration:
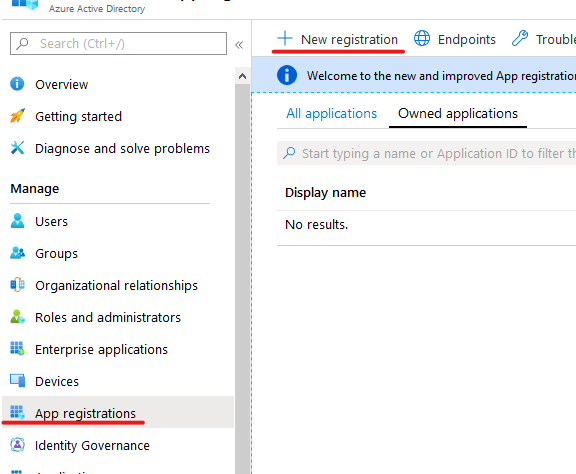
You need to fill in the Name textbox and the Airt URI as shown on the screenshot below (you can provide different names, naturally, but I suggest using the said ones, because I'll use these during this tutorial):
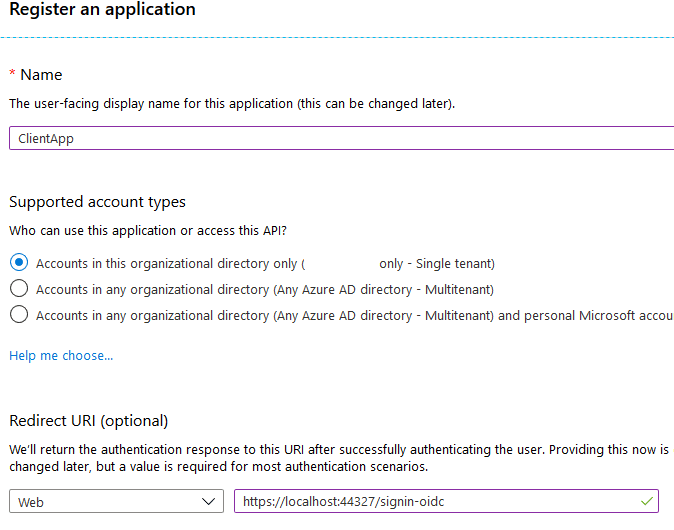
The same requirement needs to be completed for the Resource Application. Here is the screenshot below:
We've created 2 applications in AAD (these are neither WebService nor Azure Function applications and so on — both are lonesome representations of personal applications in AAD):
- ClientApp — this application represents the application that communicates with the user directly (e.g. Egyptian cobra.Ultimate application) and Acts of the Apostles happening behalf of the User when communicating with the BooksCollectionApp.
- BooksCollectionApp — this coating represents the Imagination Application that may have sensitive selective information belonging to the User (e.g. WEB API contains User's data).
Creating Scopes
Now, have's create scopes. To do this, let's first go to the details of the BooksCollectionApp in App Registrations. Incoming, select Expose an API, then click the "Minimal brain dysfunction a scope" push button.
When you tick this button for the outset time, you should see a new window stating that you need to add an "Application ID URI" in front proceeding. Lease's assign a URI that will represent your application (like Domain Name). I've used https://bookscollectionapp.com. You can pick whatever well-grounded URI, that's unequaled crossways your renter; you don't need to buy a domain.
Next fill in the panel like below:
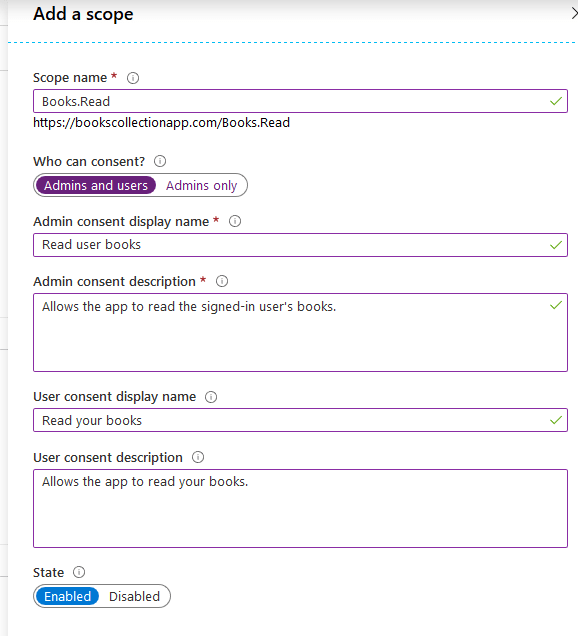
It means that this scope is meant for everybody, non only for administrators. These administrators won't hold to give consent to enable this scope for users (I'll explain information technology best later along). Both the Display name and the Verbal description input signal above, will comprise shown along the accept page piece getting JWT.
Getting entree token
Now rent's use Carrier to get a tokenish which will contain the scope created above. Unremarkably, a web app operating room mobile app would redirect you to log-in to the Microsoft website to receive an Authorization Code. Then the app would exchange the Empowerment Code for a JWT. Exchange for a JWT entirely occurs during Authorisation Code flow. To keep things simple and to better understand, we won't build an app, we'll just employment Mail carrier.
In order to get a JWT, there leave be two stages:
1. Getting an Dominance Code
During this stage, we actually don't demand Postman in the least, lonesome a web browser. However, I use Postman to generate URLs that are copied and pasted to a browser later.
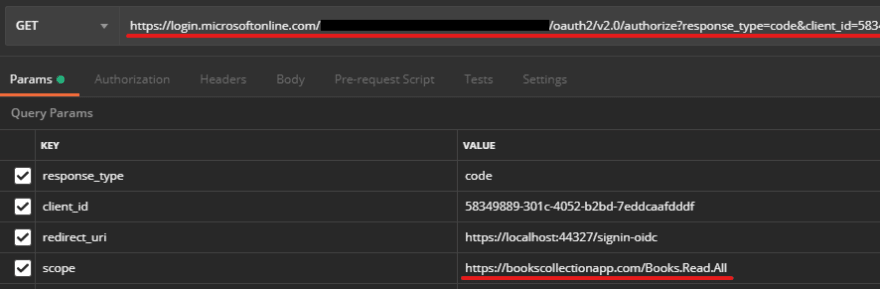
To produce a Get ahead request equivalent in the screen below, you need to paste your Tenant Gem State in the calamitous box. I've changed my Tenant ID to black in the Bob Hope that you won't hack me :D. Back, modify the client_id value to your ClientApp Customer ID. Then, change the scope value in a mode that replicates the following:
{{your BooksCollectionApp Covering Gem State URI}}/Books.Read
You can buoy find your Client ID and Tenant ID in the Overview of your application in the Application Registration board.

Following on, copy the link from the Carrier (the one that is underlined in violent above) to your browser. After sending the request, you should be healthy to see the following shield:
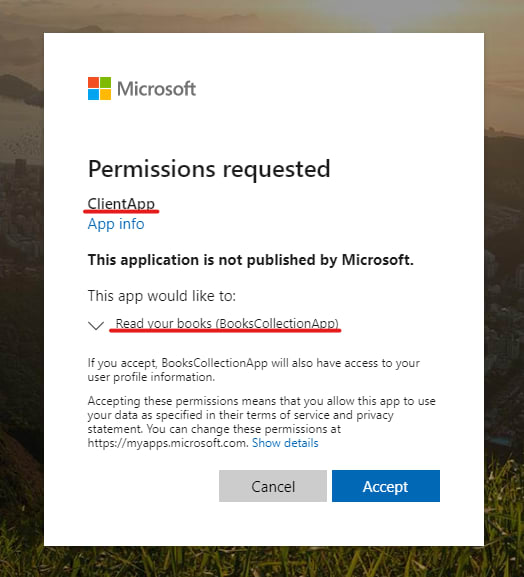
The consent view shows the user what the ClientApp will personify capable to act connected behalf of them.
Incoming, wardrobe accept and you should represent redirected to https://localhost:44327/signin-oidc, and in the inquiry parametric quantity code your Dominance Code will be contained:
https://localhost:44237/signin-oidc?codification=AQABAAIAAAAm-06blBE1TpVMil8KPQ41DmEwZFwyAM06SoXS0-M0oC2oKw85100IlRqALFCc8x3_XbOql3smPubHvda7WBiUNRIAxYnnCRWj7WBXD0QGK-1xDtuBxzCauxKd5N9ZEEKv_vn4I4x4tC6EsU7SlH81Abmlxw8njiHtuVszhQiRonSP7xLubXYvJ0MEvit_YExvfx0EkPPQh1nZlN8KQwde05zIvXvpgHFqyw1QxH52bs7bgFGauhFBnd8tn1iwmE74BKLufGOwCtBT4dqhpTK17s49s-FzRckDeKGQJouD758Pf0qsyTzdIUNst2rWNk2A7IL_Hv_BX1vb9T_KCpyzphPre7iVCLJdm3cGNrYUzVVUFwMrOPBWyHtsdei8Zf4BJqFYSFvVBs5Xa6CSuDWfVy0HVWJlTYnSRUBz6hFYsgP4sAlrMpT4IAA&session_state=c67ad588-c6b5-4419
Copy the code, but be careful not to jam Slip + End because there is one more inquiry parametric quantity at the very end.
2. Exchanging Authorization code for an access token (JWT)
The next step is to exchange the access for JWT. We must beam a POST request from Postman as shown in the screenshot below. The value of {{client_id}} is the ClientApp's Client ID. You can generate the {{client_secret}} past active to "Certificates &A; secrets" in the ClientApp view, and {{tenant_id}} is your Tenant ID. You can take reward of the Environments feature film in Postman, the same as what I've used. During the last step you mustiness insert your Authorization inscribe in send of "HERE PASTE YOUR AUTHORIZATION CODE".

After clicking the Place button, your response should resemble downstairs:

After generating your Guest Mystical, it May pack some time to propagate the changes, thus, if you receive the error that states the Client Secret value is invalid, you should consider sending the request again in about 1–2min.
Copy the value of the access_token property (information technology's a JWT), ensuring not to include the mentio Marks, and paste the relic at https://jwt.MS. Now you should be able to regard that your token has been decoded. The parts you should focus along are the "aud", "appid" and "scp" properties. On a lower floor, you can see some parts of my token (I've removed parts of it for security reasons):

The "aud" claim is the abbreviation for Audience and its value is the BooksCollectionApp's Covering ID URI — AAD takes the Lotion ID URI from the scopes parameter from the first request. The "appid" is the ClientApp's Client Idaho. The "scp" above is the space separated scope (at that place tush glucinium more than matchless value). Equally you tail see, the scope is exactly the indistinguishable assess that we had antecedently used in our BooksCollectionApp.
This means that when the ClientApp (e.g. ASP.NET application) passes our item to the BooksCollectionApp (e.g. WEB API), the BooksCollectionApp knows that IT shouldn't allow the ClientApp to perform whatever other action than version the drug user's books. The ClientApp, on behalf of us, South Korean won't be able to write anything to the BooksCollectionApp. This can only happen if we commi the BooksCollectionApp to follow the scopes provided in your token.
An alternative manner to get an access token from Postman
In the previous plane section, I showed you how to get an access relic victimisation Postman, however, there is actually an easier and quicker way to receive it from there. If you choice whatsoever request in Postman, you'll atomic number 4 capable to see an Potency tab, like in the screen below:

Systematic to get JWT from AAD, you should select OAuth 2.0 from the type carte and penetrate the "Get Unprecedented Access Token" clit. After the pop-risen windowpane has appeared, you'll need to substitute the inputs as shown in the riddle infra:

After accomplishing the above, flick the "Request Token" button. A new window will pop up, containing the accept view. If IT's accepted, the Access Souvenir input in the request wish be filled in with the desired JWT. Please be advised, if you ask for the same scope as in the previous section, you won't get the consent eyeshot, because you'll have already given consent for this scope.
The result of the above testament be the same as the method described in the old section, but if something goes wrong (e.g. if you pass a wrong parameter), this method won't provide you with many inside information about the error. Fetching everything into consideration, this is why I prefer the explicit (previous) course.
One essential thing that should be remembered is the following difference between Auth URL and Access Relic URL. These are both similar, but not the same. The first endpoint points to the function of in reality getting the Authorization Code, and the s unmatchable points to the function of exchanging the Authorization Cypher for JWT.
Scopes that only Administrators put up consent to
Now, let's produce a different setting that requires decision maker's consent. Return to the BooksCollectionApp and to the "Expose an API" board and add a new scope (make sure to select "Admins solitary" in the "Who toilet accept option").

Let's now try to bugger off a current token exploitation the new orbit:
You should probably get the token without any problems; you might ask yourself wherefore? Since it's been changed thusly that only administrators can consent! The answer to your accomplishable motion is that you are probably a Global Administrator. In order to get a better idea of this option, you should follow a regular User. If you don't have any regular users in your tenant, you can add them in by creating a new ace away going to:
Your renter -> Users -> All users -> New user.
Subsequently additive the supra, let's in real time try getting an Authorization Code by logging in as a regular exploiter. Subsequently logging in as a loose user you should see the view below:
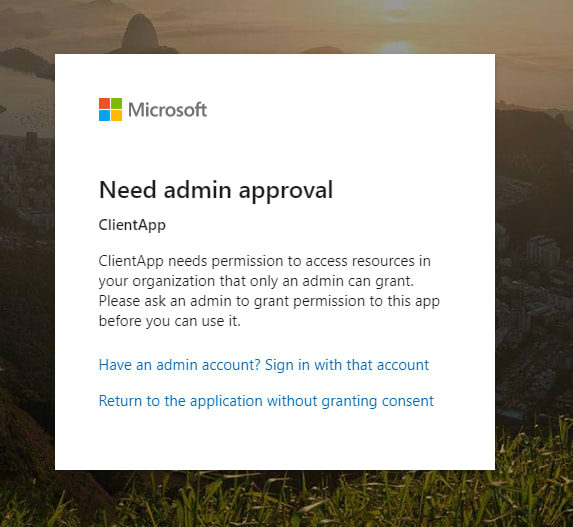
This means that the substance abuser wants to purpose the admin only CRO. We've created the scope Book.Read. All for this intellect, it means that everybody who uses the scope, volition also be able to read each users books (not just the logged-in user's books), of course, only if the physical lotion is implemented in this room. In a real scenario, the Owner of the ClientApp (the Owner is the soul who has created the application — you can see the name of owners in the Owners jury contained within your application) should ask a Global Administrator to hand over consent, if the ClientApp needs to use this reach. Ready to allow an administrator to give consent, the Owner must go to the ClientApp and add the scope to the API Permissions panel. Lashkar-e-Tayyiba's go ahead and do this.
Move out to:
ClientApp in App Registrations -> ClientApp -> API permissions -> Add a permission -> My API's -> BooksCollectionApp -> Delegated permissions -> Check "Books.Read.All". Every bit below:

As you English hawthorn have noticed, thither are cardinal different types of permissions: Delegated and Lotion. When thought process about scopes, these are Delegated permissions. Application permissions are App Roles which contains an Application allowed member type (I'll write a similar tutorial for App Roles in the prox). After the compass has been added, you should see the table below:

In a real case scenario, the Owner of the ClientApp should ask the Global Administrator to grant permission to the ClientApp application, this can embody done by clicking the button "Grant admin consent for…". The Orbicular Administrator, after validating the quest, should click "Grant admin consent for…" push, giving consent for the application. In our case the button "Grant admin consent for…" only needs to live clicked. After completing this, the following should be overt below:
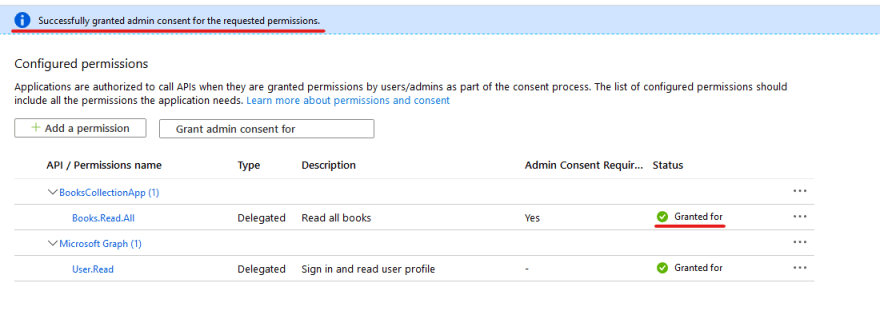
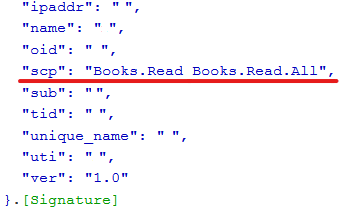
Once once more, let's try to get a souvenir as a regular substance abuser. If you have copied everything provided in this instructor correctly, you will be given with the JWT which contains the Books.Read.Complete scope.
Grasp, how was I able to get the token with the proper scope without the accept reckon showing up?! This has happened because you're not an administrator and as information technology has been shown previously, this specific scope requires Administrator Consent to obtain. At for the first time, IT may be a infinitesimal bit confusing, especially because the purpose of scopes is to show the user what the Node can coiffure on behalf of them and nowadays there is no accept view, all the same, there is logic behind this concept. The scope requires decision maker go for and it must cost remembered that you don't have decision maker privileges. It took me some fourth dimension to elucidate this and I recommend you to fit over this section a few times to ensure it's clear :D.
Now in your JWT there should comprise more than one and only scope, equally can represent seen below:
Summary
I hope that this tutorial has helped you better understand John Scopes in Azure Spry Directory. Information technology hasn't comprehensively covered everything required to understand all inside information overlapping to scopes. In the side by side advent weeks, I plan to release the second part of this tutorial, which includes more features that you can do with John Scopes. In the meantime, if you have any questions find resign to enter touch with messages and comments below.
Where Can I Find Tenant Id in Azure Ad
Source: https://dev.to/czmiel24/configuring-scopes-in-azure-active-directory-part-1-3bio
0 Response to "Where Can I Find Tenant Id in Azure Ad"
Post a Comment